
Ethereum Smart Contracts Used to Conceal Malware in NPM Packages
Ethereum has emerged as a new vector for software supply chain attacks, with attackers leveraging smart contracts to hide malicious code in popular developer tools.
Researchers at ReversingLabs discovered two NPM packages—colortoolsv2 and mimelib2—that appeared to be simple utilities but were actually designed to pull hidden URLs from Ethereum’s blockchain, directing compromised systems to download second-stage malware. By embedding these commands in smart contracts, attackers disguised their activity as legitimate blockchain traffic, making detection more difficult.
NPM, the largest package registry for Node.js, hosts millions of modules, making it a prime target for malicious actors. The packages, uploaded in July, initially seemed benign, but tapping the blockchain enabled attackers to bypass traditional security measures.
“This is something we haven’t seen previously,” said Lucija Valentić, a ReversingLabs researcher. “It highlights the rapid evolution of evasion strategies as attackers increasingly target open-source repositories and developers.”
This method builds on prior supply chain attacks that exploited trusted services like GitHub Gists, Google Drive, and OneDrive to host malware. Using Ethereum smart contracts adds a crypto-specific layer, further masking the payload.
ReversingLabs also found the packages were linked to fake GitHub repositories posing as cryptocurrency trading bots, complete with fabricated commits, bogus accounts, and inflated star counts to appear credible. Developers who installed the code risked importing malware unknowingly.
Supply chain risks in open-source crypto tooling are not new. Last year, over 20 campaigns targeted developers via NPM and PyPI, often aiming to steal wallet credentials or deploy crypto miners. The new Ethereum-based tactic shows attackers are adapting quickly to the blockchain ecosystem.
Developer Takeaways:
- Repository popularity and active maintainers can be faked.
- Even seemingly harmless packages may contain hidden malware.
- Developers must exercise vigilance when integrating open-source crypto libraries.



More Stories
Despite behaving like a tech stock at times, bitcoin continues to offer portfolio diversification benefits, according to an analyst
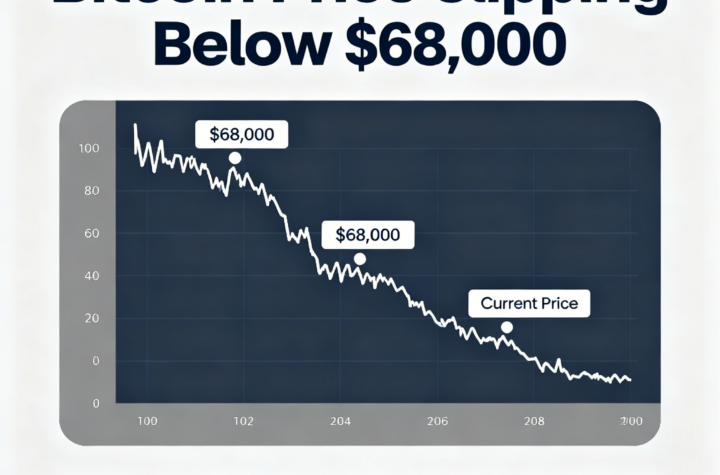
Bitcoin slides past the $68,000 mark as the dollar logs its sharpest weekly gain in a year.
Bitcoin faces a potential 30% decline as the four-year market cycle gains momentum, investment firm says.